Securely Connect Remote IoT VPC: Your Blueprint For Robust IoT Security
In today's hyper-connected world, the proliferation of Internet of Things (IoT) devices has transformed industries and daily life. From smart homes to industrial sensors, these devices generate vast amounts of data, which need to be securely transmitted and managed. Securing the connection between your IoT devices and your cloud infrastructure is paramount to protect sensitive data and prevent malicious attacks. As more devices come online, ensuring secure communication between IoT devices and the cloud is critical for protecting sensitive data and maintaining operational integrity.
The challenge lies not just in connecting these devices, but in doing so with an unyielding commitment to security. Remote IoT VPC SSH has become a critical component for securely managing and accessing Internet of Things (IoT) devices within a virtual private cloud (VPC). This guide will walk you through the process of setting up a secure connection between your Raspberry Pi and AWS VPC using SSH, ensuring that your IoT projects are both robust and resilient against evolving cyber threats. To securely connect remote IoT VPC, it's essential to understand the fundamental components of both technologies and the best practices for their integration.
Table of Contents
- The Imperative of Securing Remote IoT Connections
- Understanding the Core Components: IoT Devices and VPCs
- The Role of SSH in Secure Remote IoT Management
- Architecting Your Secure Connection: Raspberry Pi to AWS VPC
- Step-by-Step Guide: Setting Up Your Secure Connection
- Advanced Security Measures for Your IoT VPC Connection
- Overcoming Common Challenges in Secure IoT Connectivity
- The Future of Secure Remote IoT VPC Connectivity
The Imperative of Securing Remote IoT Connections
The sheer volume and diversity of IoT devices, ranging from tiny sensors to complex industrial machinery, present unique security challenges. Each device represents a potential entry point for attackers if not properly secured. The data collected by these devices often includes sensitive personal information, operational metrics, or even critical infrastructure control signals. Compromising this data or gaining unauthorized access to devices can lead to catastrophic consequences, including data breaches, service disruptions, financial losses, and even physical harm.
Consider a smart home system where an insecure connection could allow an intruder to disable security cameras or unlock doors. In an industrial setting, a compromised IoT sensor could provide false readings, leading to equipment failure or dangerous conditions. The rapid growth of IoT means that the attack surface is constantly expanding, making robust security measures not just a recommendation, but an absolute necessity. Securing the connection between your IoT devices and your cloud infrastructure is paramount to protect sensitive data and prevent malicious attacks. This is why the ability to securely connect remote IoT VPC is not just a technical detail, but a fundamental pillar of any successful IoT deployment. Without it, the risks far outweigh the benefits.
The "Data Kalimat" provided underscores this urgency: "As more devices come online, ensuring secure communication between IoT devices and the cloud is critical for protecting sensitive data and maintaining operational integrity." This statement highlights the dual importance of data protection and uninterrupted operations, both of which hinge on a secure connection.
Understanding the Core Components: IoT Devices and VPCs
To effectively securely connect remote IoT VPC, it's essential to understand the fundamental components of both technologies. Let's break down what we mean by IoT devices and Virtual Private Clouds (VPCs).
What are IoT Devices?
IoT devices are physical objects embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and systems over the internet. They can range from simple temperature sensors and smart light bulbs to complex industrial robots and autonomous vehicles. Key characteristics often include:
- Connectivity: They can connect to a network, often wirelessly.
- Sensors/Actuators: They collect data from their environment (sensors) or act upon it (actuators).
- Limited Resources: Many IoT devices have constrained processing power, memory, and battery life, which impacts the security measures they can support.
- Remote Operation: They are often deployed in remote or hard-to-reach locations, requiring remote management.
IoT devices generate vast amounts of data, which need to be processed, stored, and analyzed in the cloud. This data can be anything from temperature readings and motion detection to video streams and machinery performance metrics. The sheer volume and sensitivity of this data necessitate a highly secure communication channel.
Demystifying the Virtual Private Cloud (VPC)
A Virtual Private Cloud (VPC) is a logically isolated section of a public cloud (like Amazon Web Services - AWS) where you can launch resources in a virtual network that you define. Think of it as your own private data center within the cloud. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
Key features of a VPC relevant to IoT security include:
- Network Isolation: Your resources are isolated from other customers' traffic.
- Customizable IP Addressing: You define your own private IP address ranges.
- Security Controls: You can use security groups and network access control lists (ACLs) to control inbound and outbound traffic to instances and subnets.
- Connectivity Options: VPCs can be connected to your on-premises networks via VPN or AWS Direct Connect, and securely to the internet via an Internet Gateway.
By deploying your IoT backend infrastructure (e.g., data processing, analytics, device management platforms) within a VPC, you create a secure, controlled environment for your sensitive data and applications. The challenge then becomes how to bridge the gap between your remote IoT devices and this secure cloud environment.
The Role of SSH in Secure Remote IoT Management
When discussing how to securely connect remote IoT VPC, Secure Shell (SSH) emerges as a fundamental and highly effective tool. SSH is a cryptographic network protocol for operating network services securely over an unsecured network. Its primary use is for remote command-line login and remote command execution, but it can also be used for tunneling, TCP port forwarding, and file transfers.
SSH: Your Secure Gateway
SSH provides a secure channel over an unsecured network by using strong encryption to encrypt the connection between a client and a server. This means that any data transmitted, including credentials and commands, is protected from eavesdropping and tampering. For IoT devices, especially those like Raspberry Pi which are essentially mini-computers, SSH offers a robust way to:
- Remotely manage devices: Execute commands, install updates, troubleshoot issues without physical access.
- Securely transfer files: Move configuration files, logs, or data securely.
- Create secure tunnels: Forward network traffic through an encrypted SSH connection, effectively creating a private, secure pathway through a public network. This is particularly useful for connecting devices behind firewalls or NAT.
The "Data Kalimat" states: "A secure method for managing and interacting with IoT devices remotely using Raspberry Pi, AWS VPC, and SSH." This perfectly encapsulates the core idea. SSH acts as the secure conduit, allowing you to interact with your remote Raspberry Pi, which then communicates within your AWS VPC.
SSH Key Management Best Practices
While SSH itself is secure, its security heavily relies on proper key management. Instead of passwords, which can be brute-forced or guessed, SSH uses cryptographic key pairs (a public key and a private key).
- Generate Strong Keys: Always use strong, modern key algorithms (e.g., RSA 4096-bit or Ed25519).
- Protect Private Keys: Your private key should *never* leave your local machine and should be protected with a strong passphrase.
- Use Dedicated Keys: Generate separate SSH keys for different purposes or different devices.
- Regular Rotation: Periodically rotate your SSH keys, especially for critical systems.
- Disable Password Authentication: On your IoT devices and VPC instances, disable password-based SSH authentication and rely solely on key-based authentication. This significantly reduces the attack surface.
- Limit Access: Configure SSH to only allow connections from specific IP addresses or subnets.
By implementing these best practices, you ensure that the SSH connection, which is central to how you securely connect remote IoT VPC, remains impenetrable to unauthorized access.
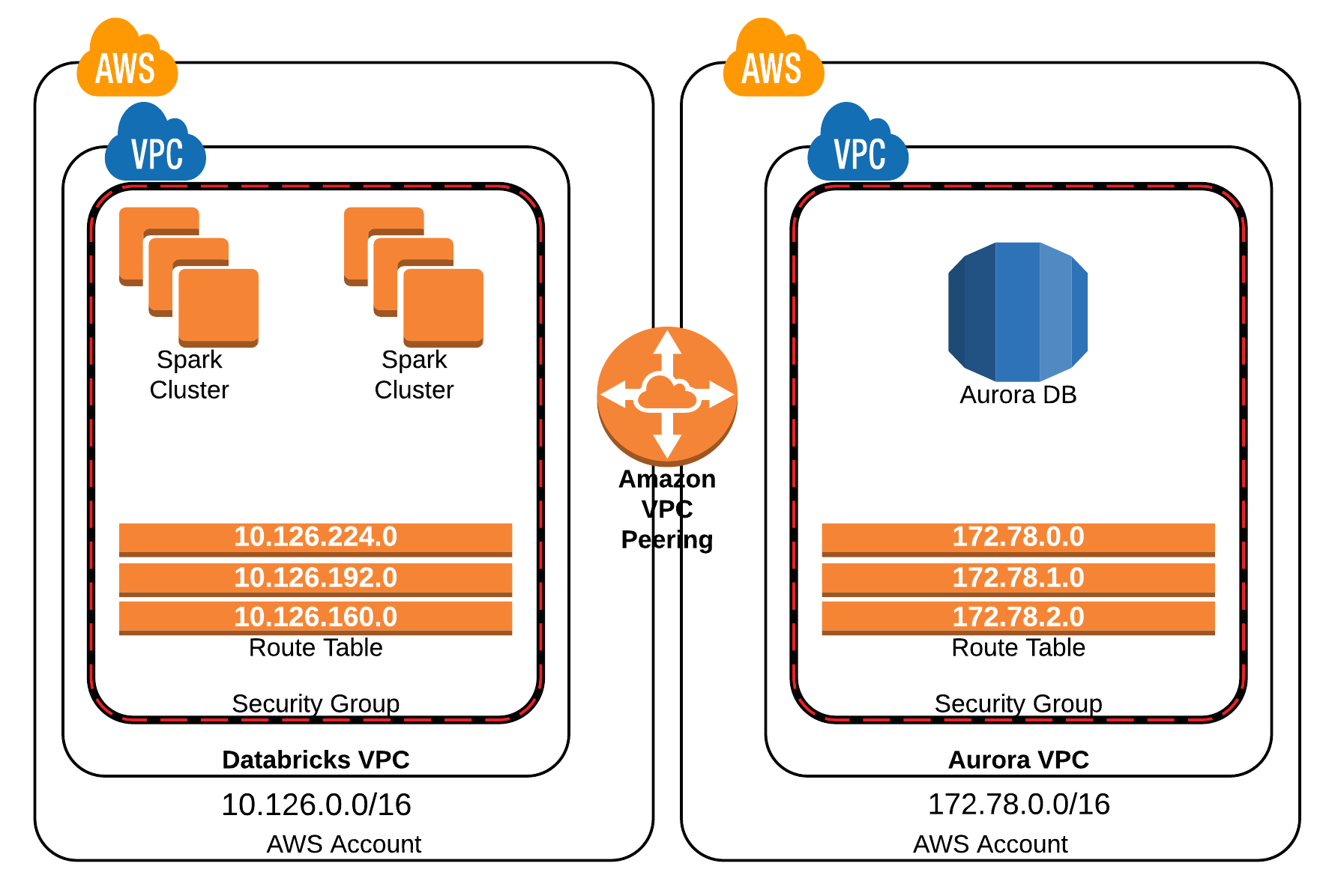
Architecting Your Secure Connection: Raspberry Pi to AWS VPC
The ability to securely connect your Raspberry Pi to a remote IoT VPC opens up a wide range of possibilities for managing and interacting with your IoT projects. It unlocks the potential to remotely manage IoT devices, which can be deployed in diverse and often challenging environments. This section explores why Raspberry Pi and AWS VPC are an ideal combination for this purpose.
Why Raspberry Pi for Remote IoT?
The Raspberry Pi is a series of small single-board computers (SBCs) developed in the United Kingdom by the Raspberry Pi Foundation. Its popularity in IoT stems from several key advantages:
- Cost-Effectiveness: Relatively inexpensive, making it accessible for prototyping and large-scale deployments.
- Versatility: Can run various operating systems (primarily Linux distributions like Raspberry Pi OS), supports a wide array of sensors and peripherals via GPIO pins.
- Community Support: A massive and active community provides abundant resources, tutorials, and troubleshooting assistance.
- Processing Power: Sufficient processing power for many IoT applications, including data collection, local processing, and secure communication.
- Network Connectivity: Built-in Wi-Fi and Ethernet make network integration straightforward.
For remote IoT applications, a Raspberry Pi can act as a local gateway, collecting data from multiple sensors, performing edge computing, and then securely transmitting aggregated or processed data to the cloud. Its ability to run a full Linux environment means it can host robust SSH clients and other security tools.
AWS VPC: A Secure Foundation
As discussed earlier, AWS VPC provides a highly customizable and isolated network environment in the cloud. For IoT deployments, its benefits are numerous:
- Scalability: Easily scale your backend infrastructure as your IoT fleet grows.
- Global Reach: Deploy resources in various AWS regions, bringing your cloud infrastructure closer to your remote devices.
- Integrated Services: Seamlessly integrate with other AWS services like AWS IoT Core for device management, Lambda for serverless computing, S3 for storage, and CloudWatch for monitoring.
- Robust Security Features: Leverage AWS's comprehensive security services, including Identity and Access Management (IAM), Security Groups, Network ACLs, and AWS WAF.
When you securely connect remote IoT VPC using AWS, you're leveraging a global, highly available, and secure infrastructure. The VPC provides the secure destination for your IoT data and the platform for your device management applications. The combination of a flexible, powerful edge device like the Raspberry Pi and a robust, secure cloud environment like AWS VPC creates a formidable architecture for any remote IoT project.
Step-by-Step Guide: Setting Up Your Secure Connection
This guide will walk you through the process of setting up a secure connection between your Raspberry Pi and AWS VPC using SSH, ensuring that your IoT projects are both manageable and secure. We'll focus on creating an SSH tunnel from the Raspberry Pi to an EC2 instance within your VPC, acting as a jump host or a secure gateway.
Preparing Your Raspberry Pi
- Install Raspberry Pi OS: Download the latest Raspberry Pi OS (formerly Raspbian) image and flash it onto an SD card. Use the Raspberry Pi Imager for an easy process.
- Enable SSH: Before booting, you can enable SSH by creating an empty file named `ssh` (no extension) in the boot partition of the SD card. Alternatively, enable it after booting via `sudo raspi-config` -> Interface Options -> SSH.
- Update and Upgrade: Once booted and connected to the internet, update your system:
sudo apt update && sudo apt upgrade -y - Generate SSH Key Pair: On your Raspberry Pi, generate an SSH key pair. This private key will be used to authenticate with your EC2 instance.
(Choose a strong passphrase for the private key.)ssh-keygen -t ed25519 -f ~/.ssh/id_ed25519_aws_iot - Copy Public Key: You'll need the public key (`id_ed25519_aws_iot.pub`) to add to your EC2 instance later. You can view it with `cat ~/.ssh/id_ed25519_aws_iot.pub`.
Configuring Your AWS VPC for IoT
If you don't have one, create a new VPC in AWS.
- Create a VPC: Go to the VPC dashboard in AWS. Click "Create VPC" and follow the wizard. Define a CIDR block (e.g., `10.0.0.0/16`).
- Create Subnets: Create at least one public subnet (for the EC2 instance to receive SSH connections) and one private subnet (for other IoT backend services, if any).
- Internet Gateway: Attach an Internet Gateway to your VPC and associate it with your public subnet's route table to allow internet access.
- Security Group for EC2: Create a new Security Group for your EC2 instance.
- Inbound Rules:
- Allow SSH (port 22) from your Raspberry Pi's public IP address (or a specific IP range if it's static). This is crucial for securely connecting remote IoT VPC.
- If using a dynamic IP for Raspberry Pi, consider using a bastion host with stricter controls or a VPN, but for simplicity here, we'll assume a known IP or a very limited time window for initial setup.
- Outbound Rules: Allow all outbound traffic (default is usually fine).
- Inbound Rules:
- Launch EC2 Instance:
- Choose an Amazon Linux 2 AMI (lightweight and secure).
- Select an instance type (e.g., `t2.micro` or `t3.micro` for cost-effectiveness).
- In "Network settings," select your VPC and the public subnet.
- Associate the Security Group you just created.
- For "Key pair (login)," create a *new* key pair for this EC2 instance (e.g., `my-ec2-key.pem`). This is *separate* from the Raspberry Pi's key. Download this `.pem` file and keep it secure on your local machine.
- Launch the instance.
- Add Raspberry Pi's Public Key to EC2:
- SSH into your newly launched EC2 instance from your local machine using its public IP and the `my-ec2-key.pem` file.
ssh -i /path/to/my-ec2-key.pem ec2-user@YOUR_EC2_PUBLIC_IP - Once inside the EC2 instance, add the Raspberry Pi's public key to the `~/.ssh/authorized_keys` file:
Replace `YOUR_RASPBERRY_PI_PUBLIC_KEY` with the content you copied from your Raspberry Pi earlier.mkdir -p ~/.ssh chmod 700 ~/.ssh echo "YOUR_RASPBERRY_PI_PUBLIC_KEY" >> ~/.ssh/authorized_keys chmod 600 ~/.ssh/authorized_keys
- SSH into your newly launched EC2 instance from your local machine using its public IP and the `my-ec2-key.pem` file.
Establishing the SSH Tunnel
Now, from your Raspberry Pi, you can establish an SSH tunnel to your EC2 instance. This tunnel will allow your Raspberry Pi to securely communicate with services within your VPC, effectively allowing you to securely connect remote IoT VPC.
There are two main types of SSH tunnels useful here:
- Local Port Forwarding (Client to Server): Forwards a port on the Raspberry Pi (client) to a port on the EC2 instance (server), which then connects to another host/port within the VPC.
This command:ssh -i ~/.ssh/id_ed25519_aws_iot -N -L 8080:YOUR_VPC_SERVICE_IP:80 ec2-user@YOUR_EC2_PUBLIC_IP- `-i ~/.ssh/id_ed25519_aws_iot`: Uses the Raspberry Pi's private key for authentication.
- `-N`: Does not execute a remote command (just forwards ports).
- `-L 8080:YOUR_VPC_SERVICE_IP:80`: Forwards local port 8080 on the Raspberry Pi to port 80 on `YOUR_VPC_SERVICE_IP` (an IP within your VPC, e.g., an internal load balancer or another EC2 instance) via the EC2 instance.
- `ec2-user@YOUR_EC2_PUBLIC_IP`: Connects to your EC2 instance.
- Reverse Port Forwarding (Server to Client): Useful if the Raspberry Pi is behind a strict firewall and cannot initiate outbound SSH connections to your EC2 instance's public IP. This allows the EC2 instance to connect back to a port on the Raspberry Pi.
This command sets up a reverse tunnel. Now, from your EC2 instance, you can connect to `localhost:2222`, and this traffic will be forwarded back to port 22 on your Raspberry Pi.ssh -i ~/.ssh/id_ed25519_aws_iot -N -R 2222:localhost:22 ec2-user@YOUR_EC2_PUBLIC_IP
(from the EC2 instance)ssh -p 2222 pi@localhost
For persistent tunnels, consider using `autossh` which automatically restarts SSH sessions and tunnels if they go down.
Testing and Validation
After setting up the tunnel, it's crucial to verify that the connection is secure and functional.
- Verify SSH Connection: Ensure your Raspberry Pi can SSH into the EC2 instance using its key.
If prompted for a passphrase, enter it. You should get a shell prompt on the EC2 instance.ssh -i ~/.ssh/id_ed25519_aws_iot ec2-user@YOUR_EC2_PUBLIC_IP - Test Tunnel Connectivity:
- If using local port forwarding, try accessing the tunneled service from your Raspberry Pi:
This should return data from the service running at `YOUR_VPC_SERVICE_IP:80` within your VPC.curl http://localhost:8080 - If using reverse port forwarding, from your EC2 instance, try SSHing back to your Raspberry Pi through the tunnel:
This should give you a shell prompt on your Raspberry Pi.ssh -p 2222 pi@localhost
- If using local port forwarding, try accessing the tunneled service from your Raspberry Pi:
- Check Logs: Monitor SSH logs on both the Raspberry Pi (`/var/log/auth.log`) and the EC2 instance (`/var/log/secure` or `/var/log/auth.log` depending on OS) for any errors or unauthorized access attempts.
By following these steps, you will successfully securely connect remote IoT VPC, enabling robust and secure management of your distributed IoT devices.
Advanced Security Measures for Your IoT VPC Connection
While establishing a basic SSH tunnel is a great start to securely connect remote IoT VPC, true enterprise-grade security requires a multi-layered approach. Here are additional measures to fortify your IoT VPC connection and overall security posture.
Network ACLs and Security Groups
AWS provides two powerful tools for network traffic filtering:
- Security Groups (SGs): Act as a virtual firewall for instances to control inbound and outbound traffic. They are stateful, meaning if you allow an inbound request, the outbound response is automatically allowed.
- Best Practice: Apply the principle of least privilege. Only open necessary ports (e.g., SSH port 22) and restrict source IPs to known, trusted locations (e.g., your office IP, or the public IP of your Raspberry Pi if static). For internal VPC communication, allow traffic only from specific security groups.
- Network Access Control Lists (NACLs): Operate at the subnet level and act as a stateless firewall, meaning you must explicitly allow both inbound and outbound rules.
- Best Practice: Use NACLs as a coarse-grained security layer. For example, block known malicious IP ranges at the subnet level or create deny rules for specific ports that should never be accessed. They provide an additional layer of defense beyond Security Groups.
Careful configuration of both SGs and NACLs is critical to ensure that only authorized traffic can reach your EC2 instance and other resources within your VPC.
Least Privilege and IAM Roles
AWS Identity and Access Management (IAM) is fundamental to securing your AWS resources.
- IAM Roles for EC2 Instances: Instead of embedding AWS credentials directly on your EC2 instance, assign an IAM role to the instance. This role grants the instance permissions to interact with other AWS services (e.g., S3 for data storage, IoT Core for device shadows) without needing explicit credentials.
- Fine-Grained Permissions: Define IAM policies that grant only the minimum necessary permissions for each role or user. For instance, an IoT device role might only have permission to publish messages to specific MQTT topics, not to delete other devices.
This principle of least privilege reduces the impact of a compromised instance or device, as an attacker would only gain access to a limited set of permissions.
Monitoring and Logging
You can't secure what you can't see. Comprehensive monitoring and logging are vital for detecting and responding to security incidents.
- AWS CloudWatch: Monitor metrics and logs from your EC2 instances, VPC flow logs, and other AWS services. Set up alarms for unusual activity (e.g., high CPU usage, unusual network traffic patterns, failed SSH login attempts).
- VPC Flow Logs: Capture information about the IP traffic going to and from network interfaces in your VPC. These logs can be published to Amazon CloudWatch Logs or Amazon S3, providing invaluable data for security analysis and troubleshooting.
- AWS CloudTrail: Records API calls made to your AWS account. This provides an audit trail of actions taken by users, roles, or AWS services, which is crucial for forensic analysis in case of a security breach.
- Device-Side Logging: Ensure your Raspberry Pi and other IoT devices also log relevant security events (e.g., connection attempts, software updates, sensor anomalies). These logs should ideally be forwarded securely to a central logging service (e.g., CloudWatch Logs) for aggregation and analysis.
By proactively monitoring these logs and metrics, you can quickly identify and respond to potential threats, ensuring the ongoing integrity of your securely connected remote IoT VPC infrastructure.
Overcoming Common Challenges in Secure IoT Connectivity
While the concept of how to securely connect remote IoT VPC is clear, practical implementation often


Detail Author:
- Name : Liliane Hodkiewicz
- Username : easter68
- Email : marjory.gulgowski@lemke.info
- Birthdate : 1993-02-23
- Address : 6707 Metz Light Apt. 504 West Flo, NY 77243
- Phone : 347-780-0909
- Company : Rippin, Mohr and Adams
- Job : Crossing Guard
- Bio : Earum provident saepe aut recusandae. Doloribus asperiores commodi omnis sit aut voluptatibus. Porro inventore possimus ut tempora.
Socials
instagram:
- url : https://instagram.com/gail.farrell
- username : gail.farrell
- bio : Voluptatem illo fugit enim aut velit esse. Quis nesciunt debitis eos dolor eos.
- followers : 2718
- following : 1177
facebook:
- url : https://facebook.com/farrell1970
- username : farrell1970
- bio : Deserunt maxime sunt rerum. Doloremque nostrum vel quis sed.
- followers : 135
- following : 2186
tiktok:
- url : https://tiktok.com/@gail9250
- username : gail9250
- bio : Aut nulla id voluptatibus ut blanditiis exercitationem dolores.
- followers : 3884
- following : 1364
twitter:
- url : https://twitter.com/farrellg
- username : farrellg
- bio : Saepe aperiam similique reprehenderit vel quam. Assumenda cumque in nobis dicta et voluptate nesciunt dolorem. Et et harum omnis illo consequatur.
- followers : 2022
- following : 975
linkedin:
- url : https://linkedin.com/in/gail3298
- username : gail3298
- bio : Voluptas necessitatibus ea est ut facere est.
- followers : 4762
- following : 1070
