Secure IoT: Raspberry Pi To AWS VPC Connection Guide
In today's interconnected world, the proliferation of Internet of Things (IoT) devices has transformed how we live and work. From smart homes to industrial automation, these tiny sensors and actuators gather invaluable data, enabling unprecedented levels of control and insight. However, the convenience and power of IoT come with a significant caveat: security. Securing the connection between remote IoT devices like a Raspberry Pi and your AWS VPC is vital for protecting your data and preventing security breaches. Without robust security measures, your IoT ecosystem becomes a vulnerable entry point for malicious actors, compromising not just your data but potentially your entire network.
This guide navigates the intricate landscape of securely connecting remote IoT devices to an AWS Virtual Private Cloud (VPC), specifically focusing on leveraging Raspberry Pi as a representative edge device. We'll delve into the best practices for establishing a resilient and private communication channel, ensuring that your valuable IoT data remains protected from end-to-end. By the end of this article, you will have a comprehensive understanding of securely connecting remote IoT VPC using Raspberry Pi on AWS, empowering you to build a robust and secure IoT infrastructure that stands up to modern cyber threats.
Table of Contents
- Understanding the Landscape: Remote IoT & AWS VPC
- Why Secure Connections Are Non-Negotiable
- Laying the Groundwork: Configuring Your Raspberry Pi for Secure Connectivity
- Building the Fortress: AWS VPC Configuration Essentials
- Connecting the Dots: Practical Secure Connection Methods
- Advanced Security Measures and Best Practices
- Troubleshooting Common Connection Issues
- The Future of Secure Remote IoT
Understanding the Landscape: Remote IoT & AWS VPC
Before we dive into the technicalities of establishing a secure connection, it's crucial to grasp the fundamental components involved. We're talking about remote IoT devices, often small, low-power computers like the Raspberry Pi, operating in diverse and sometimes untrusted environments. On the other hand, we have AWS Virtual Private Cloud (VPC), which provides a secure and isolated environment for managing these devices and processing their data within the robust AWS infrastructure. Understanding how to establish a secure connection between your remote IoT devices and your AWS VPC is the cornerstone of a reliable IoT deployment.
The Challenge of Remote IoT Security
Remote IoT devices present unique security challenges. They are often deployed in physically insecure locations, exposed to public networks, and may have limited processing power or memory, making traditional enterprise-grade security solutions impractical. These devices are frequently "headless" (without a monitor or keyboard), managed remotely, and can be difficult to patch or update in a timely manner. The sheer volume of IoT devices also creates a vast attack surface. A single compromised device can become a pivot point for attackers to infiltrate your broader network, access sensitive data, or launch distributed denial-of-service (DDoS) attacks. For instance, by integrating remote IoT VPC SSH with Raspberry Pi and AWS, homeowners can remotely control lighting, temperature, and security systems from their smartphones or other devices, highlighting the need for impenetrable security to prevent unauthorized access to personal spaces.
AWS VPC as Your Secure Foundation
AWS VPC is a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways. This isolation is paramount for security, as it means your IoT infrastructure is not directly exposed to the public internet unless you explicitly allow it. AWS VPC provides a robust and secure foundation for managing these devices, offering features like security groups, Network Access Control Lists (ACLs), and private subnetting to create layers of defense. It's the ideal environment for processing and storing the sensitive data collected by your remote IoT fleet, ensuring data integrity and confidentiality.
Why Secure Connections Are Non-Negotiable
The imperative for secure connections in the IoT domain cannot be overstated. Data transmitted from IoT devices can range from personal health metrics and home security footage to critical industrial operational data. Any unauthorized access, manipulation, or exfiltration of this data can have severe consequences, leading to privacy breaches, financial losses, operational disruptions, or even physical harm. Learn how to set up a secure connection for your IoT devices using AWS, ensuring data privacy and operational continuity. The integrity of the data is just as important; compromised data can lead to erroneous decisions, impacting automated systems or critical infrastructure.
Furthermore, IoT devices are often part of larger interconnected systems. A breach in one device can serve as a stepping stone for attackers to move laterally into your AWS environment, potentially compromising other applications, databases, or even your entire corporate network. This makes the security of each individual connection a critical link in the overall security chain. The YMYL (Your Money or Your Life) principle applies strongly here; if an IoT system controls something critical like medical equipment or vehicle systems, a security lapse could directly impact human life or significant financial assets. Therefore, establishing a robust and secure connection between your Raspberry Pi, located in a remote IoT environment, and your AWS server residing within a Virtual Private Cloud, is not just a best practice, but a fundamental requirement for responsible IoT deployment.
Laying the Groundwork: Configuring Your Raspberry Pi for Secure Connectivity
The Raspberry Pi, being a versatile and cost-effective edge device, is a popular choice for remote IoT deployments. However, its default configuration isn't inherently secure for enterprise-grade applications. The first step in securely connecting remote IoT VPC using Raspberry Pi on AWS involves hardening the device itself. This includes configuring the Raspberry Pi with the necessary software, such as a VPN client or the AWS IoT SDK, and implementing basic security hygiene.
Here’s a checklist for securing your Raspberry Pi:
- Update and Upgrade: Always start by ensuring your Raspberry Pi's operating system (Raspberry Pi OS, formerly Raspbian) is fully updated:
sudo apt update && sudo apt upgrade -y - Change Default Credentials: Never use the default username ('pi') and password ('raspberry'). Create a new user with strong, unique credentials and disable the default 'pi' user.
sudo adduser [new_username]sudo usermod -aG sudo [new_username]sudo deluser pi - Enable SSH and Disable Password Authentication: While SSH is crucial for remote management, secure it by disabling password authentication and relying solely on SSH key pairs.
(Set `PasswordAuthentication no` and `PermitRootLogin no`)sudo nano /etc/ssh/sshd_configsudo systemctl restart ssh - Install a Firewall: Use `ufw` (Uncomplicated Firewall) to restrict incoming connections to only what's absolutely necessary.
sudo apt install ufwsudo ufw default deny incomingsudo ufw default allow outgoingsudo ufw allow sshsudo ufw enable - Time Synchronization: Ensure the device's clock is synchronized using NTP (Network Time Protocol) to prevent issues with certificates and authentication.
- Install Necessary Software: Depending on your chosen connection method (VPN, AWS IoT Core SDK), install the relevant client software. For instance, for VPN, you might install OpenVPN or WireGuard clients. For AWS IoT Core, you'll install the AWS IoT Device SDK for Python, Node.js, Java, etc.
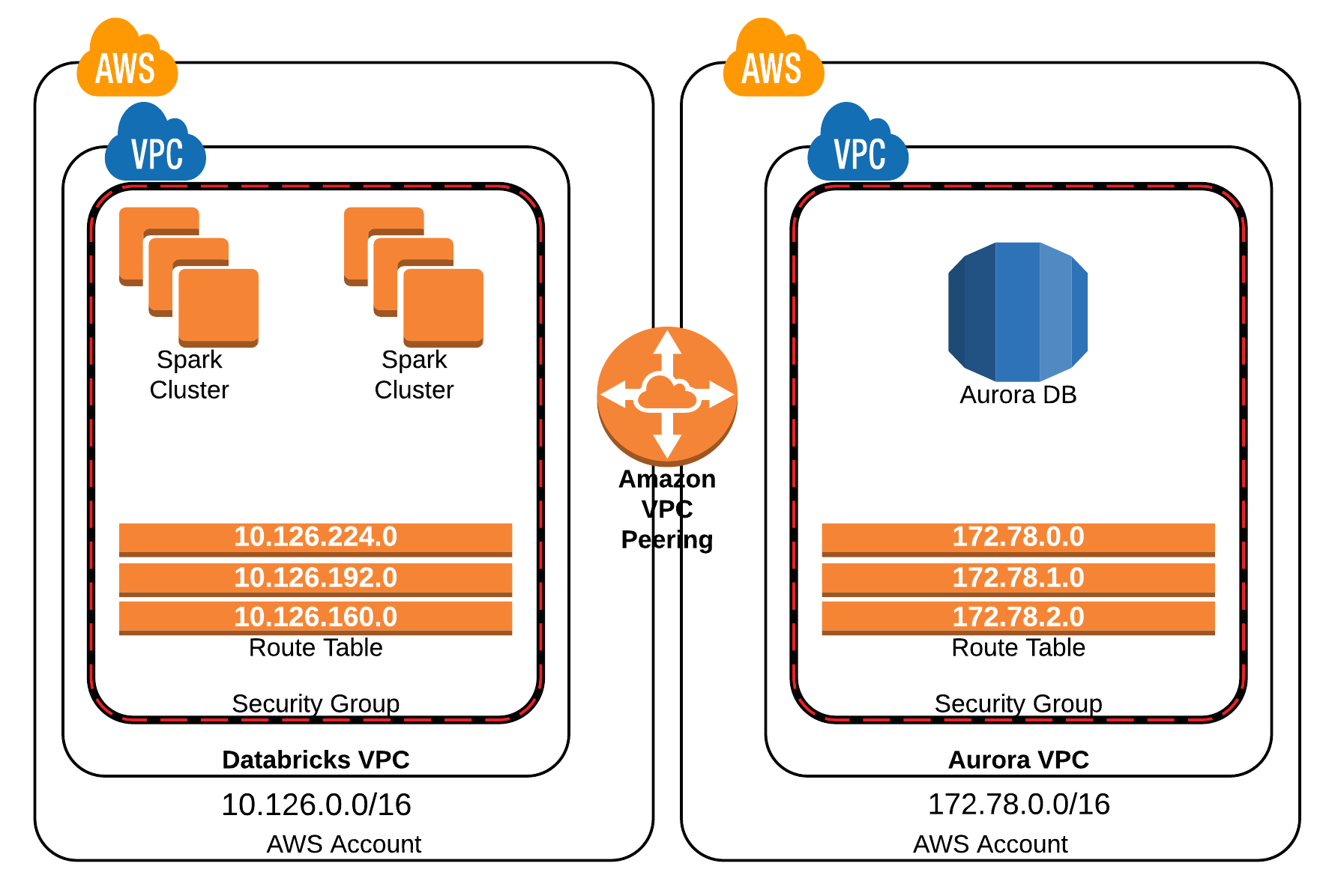
Building the Fortress: AWS VPC Configuration Essentials
Once your Raspberry Pi is hardened, the next critical step is to configure the AWS VPC, creating the necessary security groups, subnets, and routing to securely receive connections from your remote IoT devices. This article will delve into the best practices for securely connecting remote IoT devices within an AWS VPC environment, ensuring robust protection for your network. Whether you're a network administrator, DevOps engineer, or IoT developer, understanding these configurations is paramount.
Security Groups and Network ACLs
These are the foundational layers of security within your VPC.
- Security Groups: Act as virtual firewalls for your instances (e.g., EC2 instances running your IoT application backend). They control inbound and outbound traffic at the instance level. For your IoT backend, you would create a security group that only allows inbound traffic on specific ports (e.g., MQTT port 8883 for AWS IoT Core, or a custom port for your VPN server) from trusted sources, such as your VPN gateway or specific IP ranges.
- Network ACLs (NACLs): Operate at the subnet level and act as stateless firewalls, meaning they don't remember previous connections. NACLs can be used to add an additional layer of security by allowing or denying traffic to and from subnets. While Security Groups are often sufficient, NACLs provide a coarser-grained control and can be useful for blocking specific malicious IP ranges at the subnet level.
VPC Peering, VPNs, and Direct Connect Gateway
To establish secure connectivity between your remote IoT devices and your AWS VPC, especially if you have multiple VPCs or on-premises networks, AWS offers several powerful options:
- VPN Connections (Site-to-Site VPN): This is a common and highly secure method for connecting your remote IoT devices (via a VPN client on the Raspberry Pi) to your AWS VPC. You configure a Virtual Private Gateway (VGW) in your VPC and a Customer Gateway (CGW) on your Raspberry Pi (or a VPN server that the Raspberry Pi connects to). This creates an encrypted tunnel over the public internet, ensuring data confidentiality and integrity. This guide provides a comprehensive solution to securely connect remote IoT devices, specifically a Raspberry Pi, to Amazon Web Services (AWS) using a Virtual Private Cloud and VPNs.
- AWS Direct Connect Gateway: For high-bandwidth, consistent, and dedicated connections, AWS Direct Connect bypasses the public internet entirely. You associate an AWS Direct Connect gateway with your VPCs, providing a private network connection from your premises to AWS. While typically used for data centers, if your remote IoT devices are aggregated through a central gateway on-premises, Direct Connect can be an excellent choice for connecting that gateway to your AWS VPC. You can also use a virtual private gateway to extend your Direct Connect connection to your VPC.
- AWS PrivateLink: This service allows you to privately connect your VPC to supported AWS services, other AWS accounts, and on-premises applications without requiring an internet gateway, NAT device, VPN connection, or Direct Connect. For IoT, this means your devices could connect to an endpoint service in your VPC, which then routes traffic privately to AWS IoT Core or other services, significantly simplifying network architecture and enhancing security by keeping all traffic within the AWS network.
Connecting the Dots: Practical Secure Connection Methods
Securely connecting remote IoT devices involves multiple layers of networking, security protocols, and configuration settings. Here, we explore the most common and effective methods to establish this critical link.
1. AWS IoT Core with MQTT over TLS:
This is often the most straightforward and recommended approach for connecting a large fleet of IoT devices. AWS IoT Core is a managed cloud platform that lets connected devices easily and securely interact with cloud applications and other devices. It supports MQTT (Message Queuing Telemetry Transport), a lightweight messaging protocol, and enforces TLS (Transport Layer Security) for all communications.
- On Raspberry Pi: First, configure the Raspberry Pi with the necessary software, specifically the AWS IoT SDK. You'll provision X.509 certificates and private keys for each device, which are then used to authenticate with AWS IoT Core. The SDK handles the secure MQTT connection over TLS.
- On AWS VPC: AWS IoT Core is a managed service, so you don't directly configure it within your VPC in the same way you would an EC2 instance. However, you would typically have an EC2 instance or other compute resources within your VPC that subscribe to topics on AWS IoT Core to process the incoming data. You can use AWS PrivateLink to privately connect your VPC to AWS IoT Core, ensuring that traffic between your VPC and IoT Core stays within the AWS network, without traversing the public internet.
2. Site-to-Site VPN (OpenVPN/WireGuard):
For scenarios where you need a full network tunnel from the Raspberry Pi to your VPC, a VPN solution is ideal.
- On Raspberry Pi: Install a VPN client (e.g., OpenVPN or WireGuard). Configure the client with the necessary certificates and connection details to connect to your VPN server in AWS.
- On AWS VPC: Deploy an EC2 instance within a private subnet in your VPC and configure it as a VPN server (e.g., OpenVPN Access Server, WireGuard server). Ensure this EC2 instance has a security group that only allows VPN traffic from known IP ranges (if possible) or uses strong authentication. Your VPC's route tables will need to be configured to route traffic from the VPN server to your internal resources. Alternatively, you can use AWS Site-to-Site VPN, which connects your on-premises network (where your Raspberry Pi might be part of) to your AWS VPC via a managed VPN connection.
3. SSH Tunneling (for specific management tasks):
While not a primary method for continuous data streaming, SSH tunneling can be useful for securely accessing or managing a remote Raspberry Pi that is behind a firewall or NAT, by creating a secure tunnel through a bastion host in your VPC.
- On Raspberry Pi: Ensure SSH is enabled and configured for key-based authentication.
- On AWS VPC: Deploy a bastion host (EC2 instance) in a public subnet of your VPC. This bastion host should have a highly restrictive security group, only allowing SSH access from specific trusted IPs. From your local machine, you would SSH into the bastion host, and then from the bastion host, you would SSH into your Raspberry Pi via the tunnel.
Advanced Security Measures and Best Practices
Beyond the basic setup, several advanced measures and best practices can significantly enhance the security posture of your remote IoT connections to AWS VPC. This article is designed for professionals, developers, and IT administrators who need a reliable and secure connection for their IoT devices within an AWS VPC.
- Least Privilege Principle: Grant only the minimum necessary permissions to your IoT devices and the AWS resources they interact with. For AWS IoT Core, this means creating specific IoT policies that restrict devices to publishing/subscribing only to designated topics. For IAM roles, ensure they have tightly scoped permissions.
- Certificate Management: Implement a robust certificate management strategy. For AWS IoT Core, this involves rotating device certificates regularly. For VPNs, ensure VPN client certificates are properly managed and revoked if a device is compromised or decommissioned.
- Secure Boot and Firmware Updates: Ensure your Raspberry Pi devices are running signed firmware and that updates are applied securely. This prevents tampering with the device's operating system or boot process.
- Data Encryption at Rest and In Transit: While we've focused on in-transit encryption, ensure that any sensitive data stored on the Raspberry Pi itself is encrypted (e.g., using LUKS) and that data stored in AWS services (S3, RDS, DynamoDB) is also encrypted at rest using AWS KMS.
- Monitoring and Logging: Implement comprehensive monitoring and logging for both your Raspberry Pi devices and your AWS VPC. Use AWS CloudWatch, CloudTrail, and VPC Flow Logs to monitor network traffic, API calls, and device activity. Set up alerts for unusual patterns or failed authentication attempts.
- Network Segmentation: Within your AWS VPC, use subnets to segment your network. For instance, place your IoT backend processing instances in a private subnet, and only allow necessary traffic from your VPN gateway or AWS IoT Core endpoints.
- Regular Security Audits: Periodically audit your IoT device configurations, network settings, and AWS security policies to identify and remediate potential vulnerabilities.
Troubleshooting Common Connection Issues
Even with careful planning, issues can arise when securely connecting remote IoT devices to an AWS VPC. This article will walk you through the process of diagnosing and resolving issues related to securely connecting remote IoT devices to an AWS VPC. Common problems often stem from misconfigurations in network settings, security protocols, or device software.
- Network Connectivity:
- Symptom: Raspberry Pi cannot reach the internet or AWS endpoints.
- Diagnosis: Check Wi-Fi/Ethernet connection on Pi. Verify local network firewall rules. Ping public IPs (e.g., 8.8.8.8) from Pi.
- Resolution: Ensure Pi has a valid IP address, subnet mask, and default gateway. Check router settings.
- Firewall/Security Group Issues:
- Symptom: Connection times out or is refused, even if network is up.
- Diagnosis: Check Security Group rules for your AWS EC2 instance (e.g., VPN server) or the NACLs for the subnet. Ensure inbound rules allow traffic on the correct ports (e.g., 8883 for MQTT, VPN port) from the Pi's expected IP or VPN gateway.
- Resolution: Adjust Security Group/NACL rules to permit necessary traffic. Remember, Security Groups are stateful, NACLs are stateless.
- VPN/TLS Handshake Failures:
- Symptom: VPN client on Pi fails to connect, or AWS IoT SDK reports TLS errors.
- Diagnosis: Verify certificates and private keys on both ends match and are valid. Check system time on Raspberry Pi (NTP synchronization is critical). Review VPN server logs in AWS for connection attempts and errors.
- Resolution: Regenerate certificates if expired or corrupted. Correct time synchronization. Ensure correct client configuration files.
- Routing Problems:
- Symptom: Pi connects to VPN/IoT Core, but cannot reach internal VPC resources.
- Diagnosis: Check VPC route tables. Ensure routes exist from your VPN server/gateway to the subnets where your backend applications reside. Verify that the VPN server/gateway is correctly configured to forward traffic.
- Resolution: Add or modify routes in VPC route tables. Ensure VPN server's IP forwarding is enabled.
- DNS Resolution Issues:
- Symptom: Pi cannot resolve AWS service endpoints or internal VPC hostnames.
- Diagnosis: Check DNS settings on Raspberry Pi. Verify VPC DNS resolution settings.
- Resolution: Ensure Pi uses reliable DNS servers (e.g., 8.8.8.8 or VPC DNS resolver). Enable DNS hostnames and DNS resolution in your VPC settings.
The Future of Secure Remote IoT
The landscape of IoT is constantly evolving, and with it, the methods for ensuring secure connections. As edge computing becomes more prevalent, we'll see an increased emphasis on processing data closer to the source, reducing the need to send all raw data to the cloud. This trend, combined with advancements in hardware-level security (like Trusted Platform Modules on edge devices) and sophisticated AI-driven anomaly detection, will further bolster IoT security.
AWS continues to innovate in this space, offering services like AWS IoT Greengrass for local compute, messaging, data caching, sync, and ML inference capabilities on edge devices, extending AWS to the edge. The continuous development of services like AWS PrivateLink and enhanced VPN options signifies a commitment to making secure, private connectivity simpler and more efficient. The goal is to make it easier to securely connect remote IoT VPC using Raspberry Pi on AWS, from setting up your VPC to integrating AWS IoT Core and other services.
The future of secure remote IoT lies in a multi-layered approach that combines robust device hardening, secure network design within the cloud, and continuous monitoring and adaptation to new threats. Are you ready to build a robust and secure connection between your Raspberry Pi, located in a remote IoT environment, and your AWS server residing within a Virtual Private Cloud? This guide navigates the intricate landscape of securely connecting remote IoT devices to an AWS Virtual Private Cloud (VPC), specifically focusing on leveraging Raspberry Pi, providing a comprehensive solution to securely connect remote IoT devices.
Conclusion
Securing the connection between your remote IoT devices, such as a Raspberry Pi, and your AWS VPC is not merely a technical task; it's a critical investment in the integrity and reliability of your entire IoT ecosystem. We've explored the fundamental importance of this security, delved into the essential configurations for both your Raspberry Pi and your AWS VPC, and outlined various practical methods for establishing robust, encrypted connections. From hardening your edge devices to meticulously configuring security groups, network ACLs, and leveraging AWS services like IoT Core, VPNs, and PrivateLink, each step contributes to a formidable defense against potential threats.
And there you have it—a comprehensive guide to securely connecting remote IoT devices to AWS VPC using Raspberry Pi. By diligently applying the principles and practices discussed, you are not just connecting devices; you are building a resilient, trustworthy, and future-proof IoT infrastructure. The journey to a truly secure IoT environment is ongoing, requiring continuous vigilance and adaptation. We encourage you to implement these best practices, stay informed about the latest security advancements, and explore the full capabilities of AWS to further fortify your remote IoT deployments. What challenges have you faced in securing your IoT connections? Share your experiences and insights in the comments below, and let's continue to build a more secure connected world together!


Detail Author:
- Name : Mr. Darryl Lynch IV
- Username : rstanton
- Email : watsica.reinhold@walter.com
- Birthdate : 1975-12-21
- Address : 3065 Bashirian Alley Apt. 105 South Reymundofurt, KY 51365-2486
- Phone : 669.362.8566
- Company : Johns and Sons
- Job : Environmental Science Technician
- Bio : Occaecati velit neque deserunt iste. Quaerat ut cumque odit quasi maiores qui.
Socials
twitter:
- url : https://twitter.com/samantha3715
- username : samantha3715
- bio : Perferendis sunt ea eaque earum quidem quos aut. Corrupti harum voluptatem eligendi nihil sit aut id. Soluta recusandae vel est repellat totam enim.
- followers : 481
- following : 855
tiktok:
- url : https://tiktok.com/@samanthaschneider
- username : samanthaschneider
- bio : Eos accusantium beatae a sed ab qui sint. Reiciendis in in qui cum commodi.
- followers : 1531
- following : 387
facebook:
- url : https://facebook.com/samantha.schneider
- username : samantha.schneider
- bio : Vitae eos sed provident quae doloribus temporibus.
- followers : 3159
- following : 2984
